Webinars
Length: 63:00 mins
Mike Baglietto, Director, Product Marketing, AirTight Networks
Concern about wireless security is the # 1 issue impeding WLAN adoption today. This webinar discusses the evolution of current and emerging wireless threats and their impact on the enterprise, the security challenges facing IT, especially with the adoption of 802.11n, and the pros and cons of various defense mechanisms intended to address the vulnerabilities wireless introduces into your business on a daily basis.Length: 79:16 minss
Dr. Hemant Chaskar, Director of Technology at AirTight Networks
This webinar includes discussion on important Wi-Fi security issues and the solutions available to address them. Enterprises which need to secure their networks from Wi-Fi threats in order to protect their information assets, prevent unauthorized use of their network, enforce no-Wi-Fi zones, and meet regulatory compliance for themselves and their clients will benefit from this webinar.
Length: 45:00 mins
Gopinath K.N., Director of Engineering, AirTight Networks
Mike Baglietto, Director of Product Marketing, AirTight Networks
Length: 56:00 mins
Dr. Kaustubh Phanse, Principal Wireless Architect, AirTight Networks
Mike Baglietto, Director of Product Marketing, AirTight Networks
- How to identify smartphones connected to your network
- To define and enforce a smartphone access policy
- Why Mobile Device Management (MDM) alone cannot restrict unapproved smart device connections
- Controls to restrict access of personal smart devices on your network
Length:72:00 mins
Dr, Kaustubh Phanse, Principal Wireless Architect, AirTight Networks
Della Lowe, Sr. Director of Global Marketing, AirTight Networks
View this webinar to learn about :
- How to identify smartphones connected to your network
- To define and enforce a smartphone access policy
- Why Mobile Device Management (MDM) alone cannot restrict unapproved smart device connections
- Controls to restrict access of personal smart devices on your network
Length: 60:00 mins
Dr. Hemant Chaskar, Director of Technology, AirTight Networks
Tom Conklin, Managing Director, Goverment Relations, AirTight Networks
- The state-of-the art in wireless intrusion prevention technology and systems; which can be used to protect networks from WLAN vulnerabilities, including those specifically cited in the GAO report and others.
- Additional details on the WLAN risk scenarios cited in the GAO report and the recommendations in the report for processes and technology to protect government agencies networks from wireless vulnerabilities and attacks.
- Effective strategies Agencies use to protect networks from wireless risks
- How to avoid the nuisance of false alarms in wireless intrusion prevention systems.
Length: 45:26 mins
Dr. Hemant Chaskar, Director of Technology, AirTight Networks
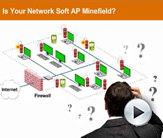
Watch this Webinar to learn:- Conventional Rogue AP vs Soft Rogue AP Scenarios
- 5 Windows Soft Rogue APs you need to be aware of
- What this means for enterprise security
- What security administrators can do about it
Length: 79:00 mins
Dr. Pravin Bhagwat, CTO, AirTight Networks
Dr. Hemant Chaskar, Director of Technology, AirTight Networks
Length: 64:00 mins
Paul Labbe, Director, Clinical Engineering, Maine Medical Center
John Foley, Senior Network Engineer, Maine Medical Center
Craig Mathias, Principal, Farpoint Group
Sri Sundaralingam, Vice President, Product Management, AirTight Networks
- Effective pre-deployment planning including predictive RF planning, RF site survey, etc
- Key best practices to follow for securing your WLAN
- Comparing integrated WIDS versus overlay WIPS
- Key criteria for selecting your WIPS vendor
- Security capabilities provided by WLAN infrastructure vendors (e.g. Cisco)